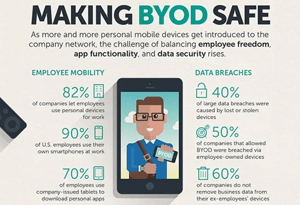
(Image courtesy Trend Micro)
Many businesses have started to make the switch from company-provided technology to Bring Your Own Device (BYOD). For business owners, this has many advantages; you don’t have to buy your workers a device to work on and the employee gets to use whatever form factor they’re comfortable with. This allows users to choose from Microsoft or Mac, smartphone, tablet, or laptop.
There are some cyber security risks you should be aware of before you apply a BYOD policy to your business. For one, these devices don’t have the same degree of protection that you’ve applied to your commercial PCs and mobile devices. You also have no control over the use of these devices outside of commercial hours.
Another challenge is with personal devices brought to work that are solely for personal use. The most common example is employees connecting their personal cell phones to the corporate wi-fi. Most companies address this challenge by creating a guest network that bypasses the commercial network and goes directly to the internet. This approach also works well for visitors to your business who require access to wi-fi but not access to your network. By adopting this approach, you can significantly reduce the threat associated with letting your workers use their devices at work.
So, how do you address this issue? First, you need to have a BYOD policy that explicitly lays outs the workers’ rights and responsibilities regarding company data on their own devices. Your policy may need to address the employees’ liabilities in using their own devices to access company information. There are also questions about what kind of IT support should be given to staff when they use their own device. For instance, who is responsible for system updates and backups? There is a lot to consider when writing a BYOD policy. Your policy should specify the following at a minimum:
- Acceptable use policy: What applications and resources are employees permitted to access from their personal devices?
- Clearly state the minimum required security controls for devices
- What components are to be provided by the Company, such as SSL certificates for device authentication
- The right of the company to alter the device by remote wiping for lost or stolen devices, as an example
- A requirement for multifactor authentication to access all company data/email on personal devices
Building a BYOD policy at your business involves many factors. You don't have to build it alone. Trust the experts at Quick Intelligence to help you write your BYOD policy.
